Media Independent Virtual Private Wireless
Mesh Networks
I SCIENTIFIC BACKGROUND
Wireless Mesh
Networking (WMN) takes advantage of the intrinsic infrastructure-free and low-maintenance
characteristics. The adoption of WMNs for supporting service-oriented
home and office networking applications has attracted explosive attention from
both industry and academia in the past a few years. Wireless mesh networking based
on IEEE 802.11 is a promising alternative to the traditional wired Digital
Subscriber Line (DSL) and Cable Modem services due to its flexibility, reliability,
ease of deployment, and cost efficiency. A WMN is mainly composed of a cloud of
distributed Mesh Points (MPs) as the backhaul. Each MP could possibly connect to
all the other MPs in its transmission range, by which the network topology is
formed. A data path with multiple hops could be created by performing MAC-layer
forwarding for the launched traffic in each intermediate node. A routing table
is maintained at each intermediate node to facilitate the MAC layer hop-by-hop forwarding,
where the MAC address of the next hop for each data path traversing through the
node is kept.
Different from the wired Internet, the WMN
infrastructure in metropolitan areas is expected to be operated by an authorized
communication company. The WMN will support multiple enterprises which lease the
access to the WMN and request to form VPNs for their registered users. Each VPN,
thus, will able support its customers and employees based on the pre-defined service
level agreement (
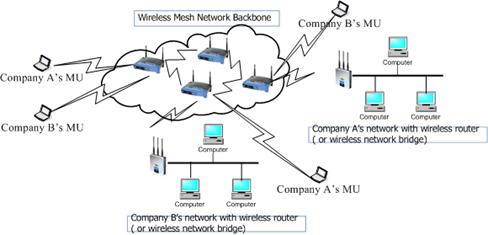
Fig. 1. The WMN-based VPN architecture applied in
metropolitan areas.
To further elaborate the functionalities and architecture of each network entity in the WMN with a VPN service support, Fig. 2 illustrates a general 4-tier architecture. The first layer is the logic tier, which accommodates numerous VPNs created by all the independent enterprises. Each VPN forms a realm (or a logic domain) defined with a group of MUs along with the corresponding QoS and privacy protection requirements. The second tier includes the mesh clients, which interfaces the logic tier and wireless mesh backhaul at the third tier. In the proposed architecture, two types of mesh clients are defined. The first type is composed of various single-user mobile devices such as laptops and handheld PDAs, etc. The other is for wireless network bridges which interfaces the mesh clients with the wireless mesh backbone.
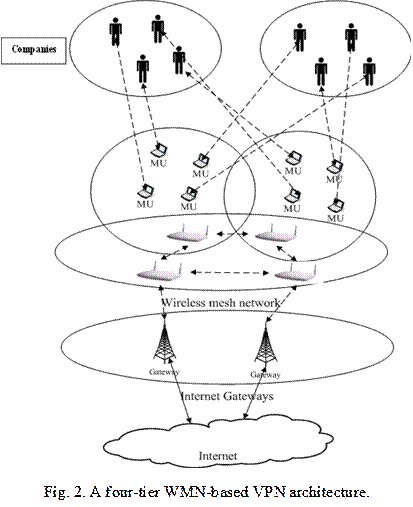 At the third layer, the mesh points (MPs)
form a multi-hop WMN backhaul with multi-radio
multi-channel wireless capabilities. From the control and management perspectives,
two types of MPs are defined. One is mesh access point (MAP) which provides all the functionalities of an
MP, including the access by mesh clients and communication with the Internet
gateways at the fourth layer. The other is the light-weight mesh point (LWMP),
which primarily serves as a “glass node” for neighbor-link communication. The lowest
layer consists of the Internet gateways, which interface the WMN with the
public Internet. In the terminology of IEEE 802.16, the Internet gateways are
simply the base stations that provide Point-to-Multi-Point (PMP) communication
mode to the surounding SSs taking the same air interfaces.
At the third layer, the mesh points (MPs)
form a multi-hop WMN backhaul with multi-radio
multi-channel wireless capabilities. From the control and management perspectives,
two types of MPs are defined. One is mesh access point (MAP) which provides all the functionalities of an
MP, including the access by mesh clients and communication with the Internet
gateways at the fourth layer. The other is the light-weight mesh point (LWMP),
which primarily serves as a “glass node” for neighbor-link communication. The lowest
layer consists of the Internet gateways, which interface the WMN with the
public Internet. In the terminology of IEEE 802.16, the Internet gateways are
simply the base stations that provide Point-to-Multi-Point (PMP) communication
mode to the surounding SSs taking the same air interfaces.
Under such an architecture, the handoff and roaming operations will be frequently triggered due to the small coverage of each MAP, high user mobility, and a large number of independent WISPs. These facts have revealed two important design issues that are unique to the WMN in metropolitan areas: the desire for a suite of light-weight handoff and roaming mechanisms, along with an efficient and robust mobility management protocol.
Let’s recall how a VPN is constructed in the conventional wired MANs. To achieve virtual private networking, an enterprise or an ISP leases the access to a set of edge node from the Internet carrier by installing the edge nodes of the carrier with a Customer Edge (CE). Each CE serves as a control box which stipulates the corresponding types of services, authority, and authentication methods, along with the custom-defined primitives and functionalities provided by the Internet carrier to the enterprise or the ISP. In VPN-supported WMNs, on the other hand, more complicated design requirements and research issues must be addressed due to some of the unique features brought up in the new networking scenario, such as the stringent requirements on high interoperability among vendor-specific wireless devices, absolute location privacy preservation of each user, and minimized handover delay. Since there could be many MAPs interconnected, it is far from scalable and cost-effective for a leasing enterprise to install all the MAPs of interest with a hardware-based VPN CE. Instead, software-based signaling mechanisms and protocols must be developed in the MAP cloud in order to achieve light-weight reconfiguration and autonomous coordination for the VPN service maintenance. In addition, since numerous independent leasing enterprises could run their business on top of the WMN infrastructure and control plane, handoff operations will certainly result in significant overhead in case there is no efficient localized authentication mechanism. At last, the issues on security protection and privacy preservation in the wireless environment must be addressed, which critically determine the feasibility and applicability of the proposed system.
II OBJECTIVES
There are many research issues related to WMNs that have been
extensively studied in the recent years. Instead of investigating into any
physical layer issue such as multi-hop interference avoidance mechanism and
channel assignment, the long-term goal of the project will be on the
development of a media independent and interoperable software platform for
achieving VPN service support, along with a suite of secure localized authentication
mechanisms with strict user location privacy preservation characteristics. We will be
particularly interested in designing a cost-efficient approach for wireless
virtual private networking implementation for home and office networking based
on WMNs, and the developed framework and software platform are expected to be
general and expandable to any wireless technology. Our short-term objectives under
the project, on the other hand, are described as follows:
- Develop an interoperable and media independent software platform based on IEEE 802.21 standard architect, where VPN services and supports are defined.
- Develop a secure localized authentication scheme with strict location privacy preservation.
- Develop a seamless and interoperable handover scheme with user mobility prediction.
Through the research efforts, we hope to generate new information and disseminate knowledge by way of interactions and collaborations with the supporting company and publications in archival journals, premier conference proceedings, technical seminars, and invention disclosures and patents. In addition, the proposed research efforts will provide a great learning environment to the participating graduate students and researchers in the aspects of Internet technologies, communication software development, and network architecture design.
III PROPOSED RESEARCH
A Development
of an Interoperable Software Platform
It is clear that the commercially available network interface controllers (NICs) adopt vendor-specific software drivers and hardware specifications, in which the integration in terms of handover decision making and Quality-of-Service (QoS) assurance will be very difficult among MUs using NICs of different vendors. Such difficulty comes from the fact that each radio interface works like a black box to the upper layer application software design, where an Internet application developer/programmer has no way to gain knowledge in the underlying MAC/PHY (Media access control layer / Physical layer) parameters and hardware specifications. On the other hand, even with the knowledge of those vendor-specific drivers and NIC hardware specifications, an application software program is still hard to real-time react to the NICs, letting alone the control of the NIC parameters. Even if the software programmer has solved the problem for a specific NIC, the developed application software will be specific to the NIC, and might not be able to migrate to a NIC of a different vendor. Therefore, it becomes a critical task to come up with an efficient and interoperable approach such that the intelligence in the user applications can be developed according to a standard library with a set of well defined Service Access Points (SAPs). The platform will serve as a shim layer working between layer 3 and layer 2, which manipulates the SAPs provided by the underlying MAC drivers of different radio interfaces. With these SAPs, another suite of SAPs will be defined for the upper IP layer by which the application software programs can make use of. The software platform will maintain the SAPs, which not only summarize the underneath layer functionalities, but also provide standardized and uniform primitives to the upper layer software package design.
 As a generic approach for achieving mesh networking, seamless
handover, and VPN service support, the project is committed to develop an
interoperable software platform, which serves as a shim layer working between layer 2 an layer 3. The software platform will enable the integration of heterogeneous
MAC protocols while providing standard primitives and functions to the upper
applications. Thus, the software platform will be essential and sufficient by customizing
the decision making process and design premise, which can effectively
facilitate our design for VPN service supported WMNs. To equip the system with
interoperability across vendor specific NICs, we will design our software
platform through the IEEE 802.21 Media Independent Handover Function (MIHF)
standard architect, such that the application layer intelligence and software packages
could be platform-independent and developed with much less efforts. The interoperable and
media-independent software platform will handle multiple NICs through an
integrated development plan upon the operation system kernel of each MP and
mobile station.
As a generic approach for achieving mesh networking, seamless
handover, and VPN service support, the project is committed to develop an
interoperable software platform, which serves as a shim layer working between layer 2 an layer 3. The software platform will enable the integration of heterogeneous
MAC protocols while providing standard primitives and functions to the upper
applications. Thus, the software platform will be essential and sufficient by customizing
the decision making process and design premise, which can effectively
facilitate our design for VPN service supported WMNs. To equip the system with
interoperability across vendor specific NICs, we will design our software
platform through the IEEE 802.21 Media Independent Handover Function (MIHF)
standard architect, such that the application layer intelligence and software packages
could be platform-independent and developed with much less efforts. The interoperable and
media-independent software platform will handle multiple NICs through an
integrated development plan upon the operation system kernel of each MP and
mobile station.
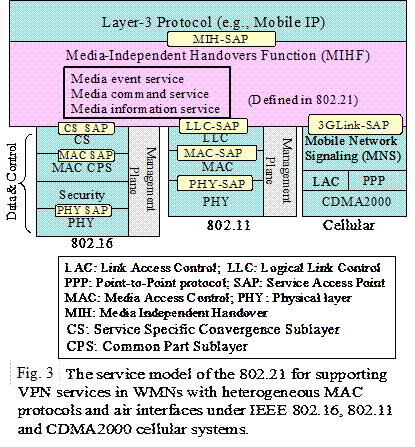
By exercising the
techniques of Linux kernel and open source codes of wireless card drivers such
as Mad Wifi, the SAPs can be defined according to the 802.21 MIHF standard architects
between IP and the proposed software platform as well as between the proposed
software platform and the attached MAC layers, as shown in Fig. 3. With the
standardized SAPs, the users can develop their intelligence for handover,
security, and throughput enhancement schemes through application layer
software.
B Design of a Localized
and Location Privacy Aware Authentication Algorithm
User authentication is an essential and unique issue in the scenario of achieving seamless handover among MAPs of common or different WISPs. A secure, priacy-preserving, and localized user authentication mechanism is required not only for the avoidance of illegitimate accesses of network resources, but also for the enterprise security and user privacy that are intrinsic to the success of home and office WMNs.
Currently,
the best practice of ensuring security in wireless networks is by way of the authentication,
authorization and accounting (AAA) framework [1], where an AAA server is
adopted to perform authentication, authorization, and collect accounting data
for each user requesting for the Internet access [2]. Based on the AAA
framework, several user authentication schemes for communication networks have
been proposed in the past decades. Lamport [3] proposed the first well-known
password authentication scheme which uses a password table to achieve user
authentication. Hwang and Li [4] presented an ID-based user authentication
scheme by taking advantage of smart cards, although the passwords in their
scheme were not low-entropy. The state-of-the-art
authentication mechanisms in the current 3G communication systems are subject
to extensive signaling of authentication requests among the handoff MU, visited
network, home network, and the AAA server. This motivates the development of a localized
authentication mechanism that can be performed locally at each MAP without any
on-line intervention of the AAA server.
To our best
knowledge, very few approaches have been reported to achieve localized
authentication for handover across wireless LANs (WLANs). The representative
schemes can be seen in [5] and [6]. In [5], an authentication protocol based on
a public-key certificate structure was proposed to achieve an efficient
localized authentication for inter-network roaming across wireless LANs.
The efficiency of the scheme comes from the fact that the AAA communication
overhead incurred in a handoff process can be reduced. Baek et al [6] proposed
a localized AAA protocol to retain the mobility transparency as the network
mobility (NEMO) basic support protocol and to reduce the cost of the AAA
procedure. In addition to providing mutual authentication, the proposed AAA
protocol prevents various threats such as replay attack, man-in-the-middle
attack, and key exposure.
Another important
issue is user location privacy. The current WLAN technology cannot avoid the
leakage of a mobile user's (MU's) location information such that an adversary
can easily track the MU's physical location. For example, an adversary can discover
when an MU visited a specific MAP and how long the MU stayed. The adversary can
also obtain when the MU moved from one MAP to another. Even if a trusted
security mechanism is in place, the adversary can still trace the location of
the MU over time by tracing the MAC address at the link layer, which is the
unique address of the network device that can be used to identify a MU.
Intuitively, a MU could frequently change his/her MAC address to avoid being
traced (although it is technically difficult to achieve by a general user), however,
it could still be vulnerable to attacks with network traffic analysis. The
reason is that generally a MU's Internet surfing habits and preferences are
deterministic and almost not time-varying. In addition, dynamically changing
MAC addresses concerns physical network interface reconfiguration, and is not possible
for the majority of MUs. Even if changing MAC addresses is possible, the MU can
still be traced during the period when the MU's MAC address stays static. Thus,
the threat on location privacy cannot be easily mitigated by using the state-of-the-art
available techniques. The task of location privacy preservation is still an open
question in spite of its imminent importance.
A number of studies
have aimed at the location privacy issues in mobile wireless networks and
proposed some countermeasures under different application scenarios [7-12].
However, these studies for location privacy are conducted at either on or above
the network layer. When an attacker is present in the link layer domain,
attacks can be launched by tracking location of any victim transparent to all
the higher layer privacy preservation strategies. The study in [13] overcomes
the link-layer privacy issue, where the transmitted link-layer packets are
encrypted by a shared session key between the MU and the access point. Due to
the nature of broadcast in wireless networks, any party located in the same
link layer can receive these encrypted packets. However, without the
corresponding session key, no one except the real destination can recover the
encrypted packet. Therefore, the location privacy in presence of link-layer
tracing can be protected. However, such an approach does not consider the
situation that once the current shared session key is compromised,
all the previous packets' privacy will be disclosed. As a result, the location privacy
information on how long the MU has stayed at the current location will be
deprived.
In order to improve
the resilience on the compromise of current link-layer location privacy under
localized authentication, the project is committed to develop a novel anonymous
mutual authentication protocol with provable perfect forward link-layer
location privacy. The proposed protocol is characterized by employing a suite
of defense-in-depth strategies such that even though an attacker has corrupted
the protection of current location information of a MU, he still cannot know
how long the MU has stayed at the current location. The proposed location
privacy aware localized authentication scheme will be characterized by the
following features.
(1)
The security notions that model the perfect forward link-layer location
privacy will be created. With the proposed model, the location privacy is
defined such that even though a MU's current location is compromised for some
period of time, the attacker could be resisted from obtaining how long the MU
has stayed in the current location. Thus, the MU's historical location information
is taken as an important issue to be protected, and is treated independently
from the current physical location information. To the best of our knowledge,
this is the first effort in the literature for formalizing user link-layer
location privacy.
(2)
With the proposed security model, we will design a novel anonymous
mutual authentication protocol between the MUs and the MAP by using location-aware
key and time-aware key techniques. The proposed location- and time-aware keys
can help the MUs and the MAP authenticate each other and negotiate a shared
session key without knowing the real identity of each other.
(3) The proposed location
privacy aware localized authentication implementation adopts a two-factor
authentication protocol to determine whether or not the handoff MU can be authenticated
without any intervention of the AAA server, where an authenticated key exchange
can be provided locally between the home and the visited network domain.
(4) With the support of 802.21 signaling mechanisms, user credentials and cryptographic tips for enabling localized authentication could be exchanged through the shim layer with the minimum efforts in revising the IP layer software artifacts. In this case, a WISP can customize and differentiate the security requirements of each class of service with an interoperable and standardized approach.
C Seamless Handover among MAPs
Based on the proposed software platform and localized authentication algorithm, the project will develop an intelligent handover algorithm for supporting user mobility and frequent handover events. To develop the intelligence in the user mobility prediction, we will manipulate a Markov-chain based parameter training process working at the 802.11 access point to estimate the timing for performing pre-handover for a mobile station (i.e., the setup of a new link to the foreign network domain). The developed network-assisted handover scheme will be able to realize the user preference in the handover strategy, where the user can customize through the application software in its mobile station. Such a design will be norm in the future wireless Internet services in home and office networking, where the proposed software platform will be more than essential for achieving the goal.
In specific, the following two topics will be investigated:
(1) Mobility Prediction: Motivated by
the fact that user mobility is mainly dominated by geography, such as streets,
hotspots, and buildings/constructions, we plan to investigate a Markov chain
based parameter training mechanism at each MAP to gain knowledge of the user
mobility pattern in the coverage of the MAP. Since the obtained
parameters through the training process are specific to the geographic
arrangement of the MAP coverage, we expect much better accuracy in achieving
the desired performance in the handoff process. The performance of the
proposed scheme will be independent of which user mobility model is assumed
since the MAP derives the user mobility pattern through the historical user
mobility record.
(2)
Handover Decision Making: We will first define the capacity of each MAP
according to its historical channel conditions and with the attached mobile
stations. By jointly considering the macro-mobility prediction and capacity of
each MAP, a suite of cost functions and preference metrics for the handover
decision making process will be developed. We anticipate that the
signaling the computation will be supported in proposed software platform and
the network processor IXP425 board, respectively.
Our ultimate target is
to bring together all the aspects and come up with a complete system for
achieving seamless handover based on the proposed MIHF software platform and localized
authentication mechanism with user location privacy preservation. We
will conduct extensive analysis for performance modeling in terms of error
propagation from the signal detection and the induced error in the measured
handoff delay. The analysis will be based on Maximum Likelihood
(ML) estimation introduced by Gagliardi and Thomas. The estimation can be
performed to derive the p.d.f. of the estimated signal-to-noise ratio for M-ary
PSK modulation over an AWGN channel. Therefore, when the handover decision is made
according to the sensed signaling to noise ratio, the analysis can return the
expected error in terms of handover delay.
IV METHODOLOGY
The proposed schemes and algorithms will be formulated
and modeled through mathematical formulation, and solved and validated through simulation.
Taking advantages of the optimization tools (CPLEX and Matlab) and high-end
workstations derived using the funds from the Canadian Foundation for
Innovation (CFI), we expect to develop large-scale
network performance simulators for examining the developed approaches on the localized
authentication and handoffs.
For achieving the proposed interoperable software platform, the design procedure is in the following. Firstly, we will develop a prototype by implementing the shim layer of IEEE 802.21 between layer 3 and layer 2, which forms the backbone of proposed software platform. So far, SparkMatrix has completed porting of 802.11 NICs of Mad Wifi on Linux kernel 2.4.21 on stand-lone PCs. As a part of the project efforts, we are going to report the Mad Wifi driver on an IXP425 network processor using Linux kernel 2.6, such that the developed prototype can be more ready for commercialization. To accommodate more versions of 802.11 NIC by different vendors into the software platform, we will contact with Linksys Inc. and Speedstream Inc. to obtain the source code of the NICs under a mutual agreement and authorization. We are also planning to extend the current platform to IEEE 802.16 paradigm in order to extend the current project to a wider scenario. We plan to purchase a WiMAX Mini-PCI Evaluation Kit from Wavesat Inc. provided the success of the prototype development.
Secondly, we will develop a novel framework of service accesses and data aggregation for implementing the IEEE 802.21 standard, where the events, commands, and information services will be defined and mapped to the proposed software platform. Based on the standard software platform, we will develop the required VPN features such as virtual access point (VAP), user defined primitives/functions, and localized authentication with location privacy preservation. Our ultimate target is to bring together all the technological aspects and come up with a complete system and service provisioning framework for achieving VPN service support in 802.11 based wireless mesh networks.
One of the key mathematical methods that we will be
using in our research is optimization. We will optimize the
system parameter settings through a cross-layer design, and the corresponding optimization tools such as
GAMS, CPLEX, and search heuristics will be utilized to solve problems in parameter
selection and tuning. The parameters we are interested include the time length
between the instant of setting up a new link and the instant of tearing down
the old link during a handover process. The two design issues will be critical
in the effort of heterogeneous network integration. This will be exercised
particularly when the application layer software programs try to take advantage
of the primitives provided by the MIHF shim layer, and when any intelligence is
going to be installed in the MIHF layer as build-in reconfiguration mechanisms,
which will be functioning when the application software does not specify any
input parameter value. Since the formulated problem could be non-linear, we
plan to use GAMS to solve and the result will serve as a benchmark for that by
any developed heuristic algorithm, such as Tabu search and Lagrange relaxation.
For performance
modeling, we will apply some advanced queuing techniques to study access
control, call admission control, mobility prediction, and handover over
wireless networks. The Markov Modulated Poisson Processes (MMPP) model has been
recognized as an accurate and practical tool in traffic pattern prediction.
MMPP will be used to model the call arrivals upon a cell, which concerns the
blocking probability, handover delay, and packet loss rate for each handover
request.
For the user
micro-mobility prediction, we will assume that the statistic information on
user traffic pattern in a hotspot can be obtained at the MAP, and the MAP will
analyze the user moving statistics and obtain the parameters through a Markov
chain model. We first define the distance of each point within the hotspot from
the AP as the state of the Markov chain. The moving statistics at the MAP is
interpreted as the sensed signal strength for a single mobile station. By
observing the sequence of sensed signal strengths for a given time window, the
transition probability of each pair of states can be obtained, with which the
Markov chain is constructed. With the Markov chain, the MAP can estimate when
to set up a link to the new network domain for a MS at the boundary of the
hotspot.
We will use C/C++
language and combine with MATLAB to build the event-driven simulation
environment. The simulation will be run
on the OMNeT++ [14] simulator to validate our mathematical model.
REFERENCES
[1] C. De Laat, G. Gross, and L. Gommans, “Generic AAA
Architecture,” RFC 2903, March 2000.
[2] B. Aboba, et. al. ”Extensible Authentication
Protocol (EAP)”, RFC 3748, June, 2004.
[3] L.
Lamport, “Password Authentication with Insecure Communication,” Communication
of ACM, 24 (11), pp. 770 - 772, 1981.
[4] M. S.
Hwang, and L. H. Li, “A New Remote User Authentication Scheme Using Smart
Cards,” IEEE Transactions on Consumer Electronics, 46 (1), pp. 28 - 30,
2000.
[5] Y. Desmedt and Y. Frankel,
“Shared generation of authentication and signatures,” In Advances in
Cryptology - CRYPTO’91, Springer-Verlag, Berlin, pp. 457-469, 1991.
[6] Z. Cao, H. Zhu, and R. Lu, “Provably secure
robust threshold partial blind signature,” in Science in China Series E,
vol.35, no.12, pp.1254-1265, 2005.
[7] F. L. Wong and F. Stajano, “Location privacy in
bluetooth”, in Proc. of the 2nd ESAS, LNCS 3813, pp. 176-188,
Springer-Verlag, 2005.
[8] J. Girao, B. Lamparter, M. Liebsch, and T.
Melia, “A practical approach to provide communication privacy”, in Proc.
IEEE ICC 2006, Vol. 5, Istanbul, Turkey, June 2006, pp. 1965-1970.
[9] P. Nikander, J. Arkko, and B. Ohlman, “Host
Identity Indirection Infrastructure”, in Proc. of The Second Swedish
National Computer Network Workshop 2004 (SNCSW 2004), November 2004.
[10] I. Stoica, D. Adkins, S. Zhuang, S. Shenker,
and S. Surana, “Internet indirection infrastructure”, in Proc. ACM SIGCOMM
Conference (SIGCOMM 2002), August 2002, pp. 73-88.
[11] M. Gruteser and D. Grunwald, “Enhancing
location privacy in wireless LAN through disposable interface identifiers: a
quantitative analysis”, Mobile Networks and Applications, Vol. 10, No.
3, pp. 315-325, 2005.
[12] L. Huang, K. Matsuura, H. Yamane, and K.
Sezaki, “Enhancing wireless location privacy using silent period”, in Proc.
IEEE WCNC 2005, Vol. 2, New Orleans, LA, USA, March 2005, pp. 1187 - 1192.
[13] F. Armknecht, J. Girao, A. Matos, and R. L.
Aguiar, “Who said that? privacy at link layer”, in Proc.
IEEE INFOCOM 2007,
[14] OMNeT++ manuel, http://www.omnetpp.org/doc/manual/usman.html