Activities
Activities are small hands-on activities you can do to experience security and privacy first-hand and potentially discuss it with other people within and outside of the course. They are intended to be short hopefully taking only 5-10 minutes to complete, but with the opportunity to explore more if you are interested in doing so.
Not graded: USEC students are not requried to complete the activities. They are not marked and do not impact your final grade. The activities were copied from a Computer Security course and some outreach activities. I have tried to remove mention of grading, but appologies if there are still some grading-related wording in them.
I recommend:
- Completing the activities with other people you can discuss them with
- Try answering the self-reflection questions
- You are also welcome to share activities with people outside the course
Subsections of Activities
Block third party content
Install a Javascript blocker and then experiment with what happens when various parts of a website are blocked and unblocked.
Steps
The instructions below assume Firefox, but should work for several different browsers.
- Install one of the following blockers in your browser.
- uMatrix - recommended
- noScript
- Visit a large for-profit news website such as:
- Unblock select Javascript sources. Most blockers default to blocking all Javascript from third parties. Try unblocking different Javascript sources one at a time, remember to re-load the website between each change to the blocking so you can see changes.
- Visit a large publicly funded news website such as:
- Repeat step 3.
- Either keep or delete the plugin. If you keep it, make sure you know how to open a new plugin-free profile (firefox -p) or have another browser available as the plugin will break banking websites.
Self-reflection questions
- How did the two types of sites (for-profit and public) differ in terms of the amount and types of Javascript being used?
- How many different Javascript sources did you have to unblock to make the site usable?
- Did you feel like you would be able to selectively load just the parts of a site that you wanted to?
Other things to try
Try out other websites that you use frequently. The University of Waterloo for example. Large complex sites like Facebook can also be interesting to block bits of to see what happens.
It is your data, so you should have the right to it. The introduction of the Data Protection Directive (1995) in Europe caused several companies to start making users’ data available. Back in 1995 they sometimes sent printed copies in the mail, but now most large companies offer you the right to access your own data for free digitally.
In this activity you will be:
- Selecting a company/organization
- Going through the process to request your own data
- Downloading the data
- Opening the data
Potential places to get data
You may download your data from any internet service that supports it. The following is a list of companies that support data download and a link to get you started.
Open the data
Open up the data in whatever format it is in. You may need to try some different file formats. Below are some things you can try looking for in the data:
- Logins to your account. Sometimes these include GPS locations and/or IP addresses. Are they accurate?
- Lists of friends. Do you still know all these people?
- Photographs uploaded.
Reflection questions
- What was the download process like? Did it feel easy and effortless or was extensive technical experience needed?
- How useful is the data? Now you have your own data on your computer, do you feel like you could actually use this data for anything?
- What surprised you most about the process of downloading your own data?
Other things to try
If you have some extra time try:
- Downloading data from more than one source and comparing the file structures.
- Try uploading some of your data onto another platform. In theory some of these download platforms are intended to allow users to move their data between companies.
Learn more
Opt-out of data usage or collection
You often have the right to opt-out of data collection and usage. Unfortunately opting out can be rather complex. But in order to comply with various laws, and to claim they are doing right by consumers, most companies do have a functional path to opt out of various things.
A common opt-out is cookies and other types of web tracking. In order to claim that opting out is a reasonable and realistic thing for consumers to do, advertisers form alliances where consumers can (theoretically) opt out of tracking by all members on one page.
Steps
Try opting out of cookie tracking using one of the two websites below. Both of these sites are run by advertising networks. Do your best to opt out of as many trackers as possible.
Reflection questions
- What was the experience like?
- Are you confident that you opted out correctly without making any errors?
- Are you confident that you will no longer be tracked by these companies?
Other things to try
Try opting out of some other form of tracking or marketing. Below are some ideas of what to try:
- Car: most modern cars send information back to their makers. Try finding out what information is sent and opting out of its secondary usage as much as possible.
- Robotic Vacuum: most robot vacuums map homes and send data back
- TV: Most modern smart TVs collect detailed information about what shows are being watched. They may also add behavioral marketing based on collected data.
- Smart Meters: Likely installed by the energy company. Find out if your house, apartment, dorm, condo, or other residence has a smart meter.
If you have done the Javascript activity already. Try installing UMatrix again and then opting out using one of the two pages above. Consider how different privacy protection technology may interfear with each other.
Learn more
Modify Website Content
In this activity you will be modifying a live website, essentially creating something you could screenshot and would look 100% real but is completely fake. Please use this information responsibly and as a lesson about trusting screenshots of websites.
Software: Instructions are written for BlueSky and Chrome but should work with most major browsers and social media platforms.
Steps
Modify BlueSky Post
- Go onto BlueSky (or another social media site) and find a specific post you would like to modify.
- Right click on the part of the post you want to change and select “Inspect”.
- The browser should have brought up the HTML assocated with that part of the page. Below is a screenshot of me doing this with a Krebs on Security post.
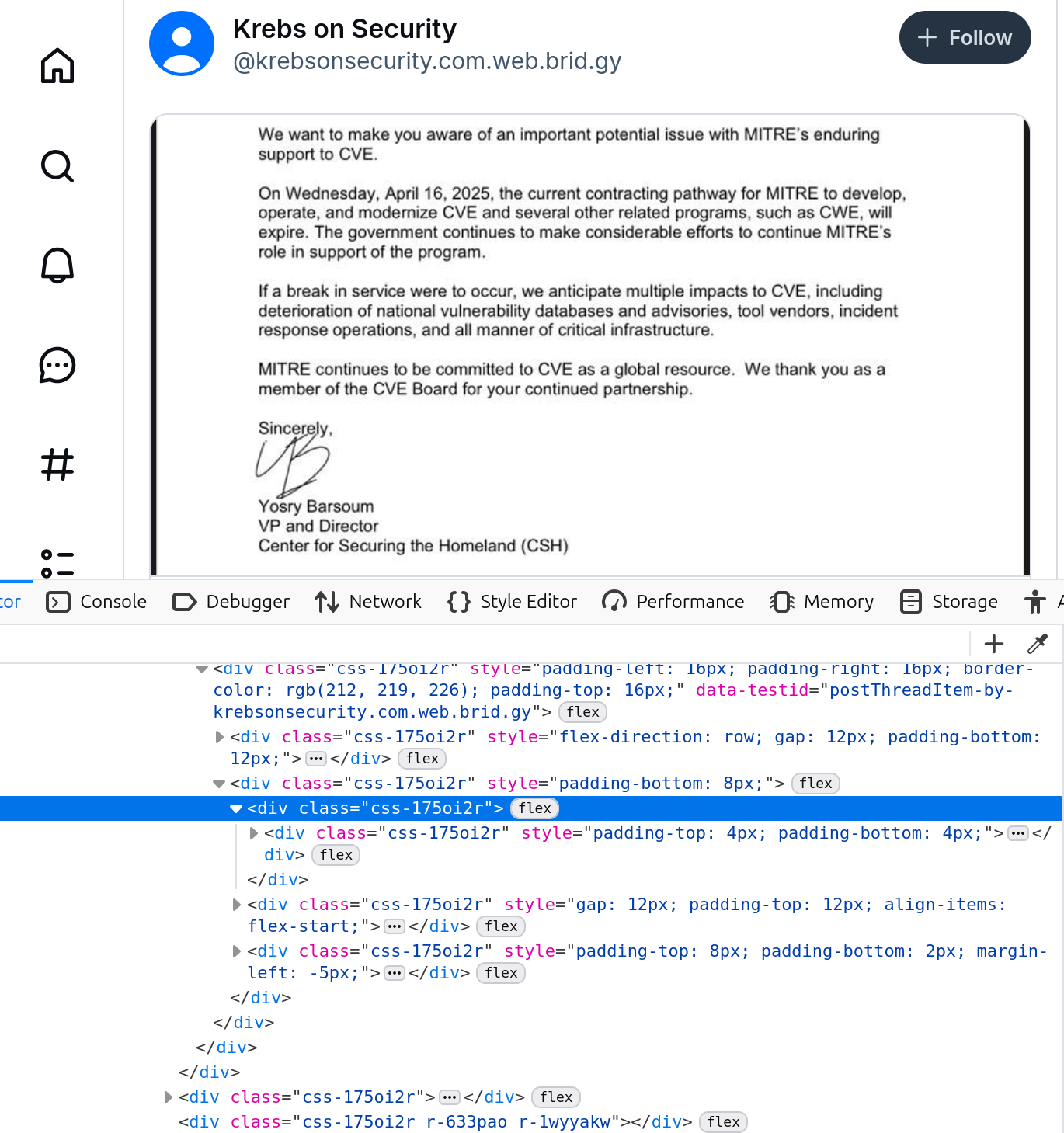

- Find the line you want to edit, right click on it, and select “Edit as HTML”. You can now edit the text or just add some.
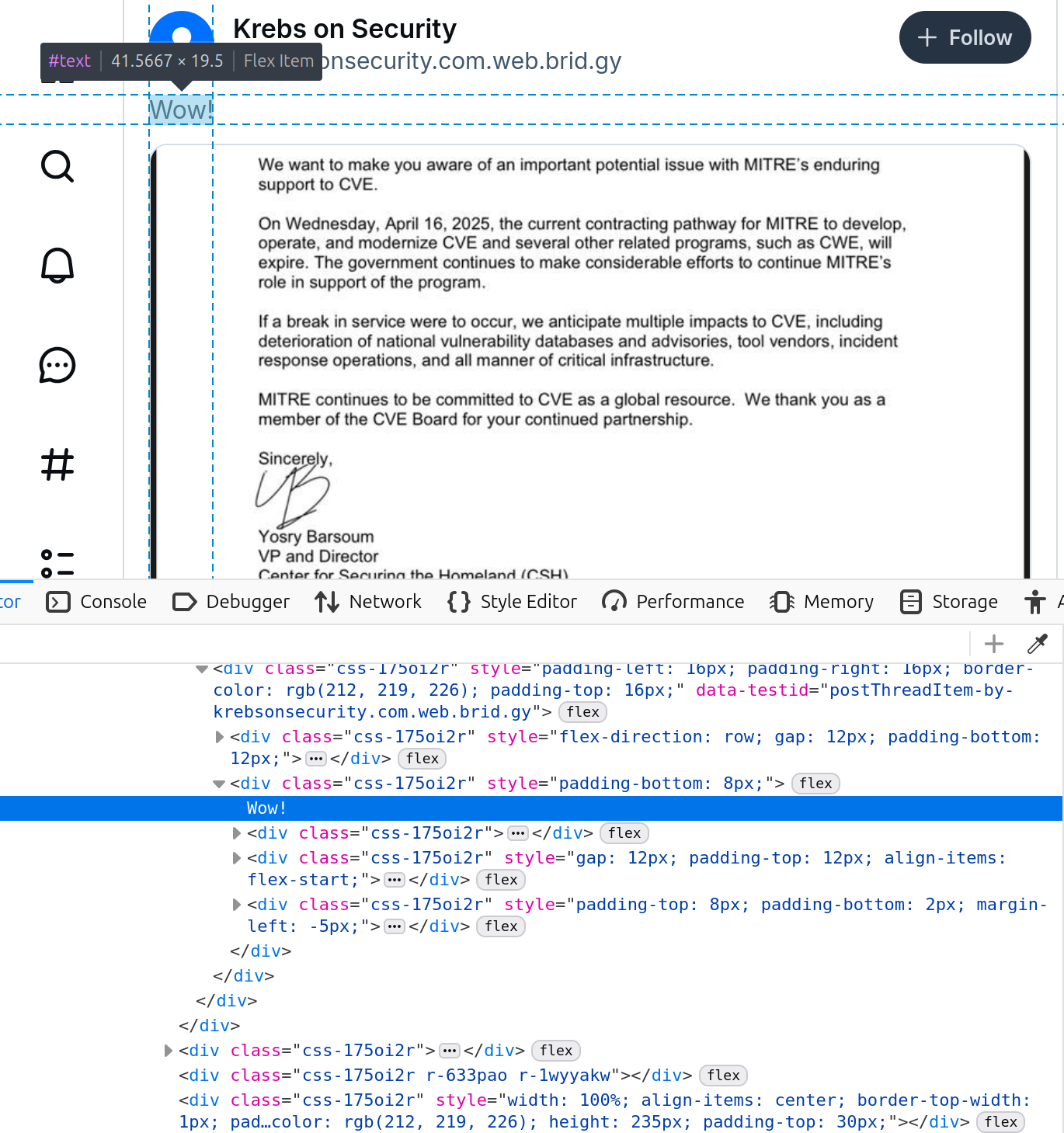

- Look at the resulting page.
Modify Javascript
Modifications are not limited to just HTML. It is very possible to modify code on the page and change its behavior.
Chrome is required for these instructions. It is possible in Firefox but quite annoying.
- Visit this practice page
- The page loads Javascript code. To see it, right click on “Submit” and click “Inspect”. Then select “Sources” in the developer console.
- Figure out what you need to enter into the text box to get the page to say “Hello World” at you.
- Change the Javascript so that any text will cause “Hello World” to appear.
Reflection questions
- Reflect on the following two prompts:
- Screenshots are often used as evidence in news articles and social media posts. Especially for content that has been deleted.
- Websites are made of a mix of client code (HTML, JavaScript) and backend server code (PHP, Ruby, Python). Client-side checks are used quite often by websites.
Other things to try
Try removing page element that you find annoying. Technology like Ad Blockers are just automatically doing what you can do manually. Try loading a page that has a large banner or ad at the top and then remove it. You will often see me doing this at the start of class. I like to make news articles on the screen easy to read, so I often remove unecessary page elements and change the text width.
Look at client-side checks.
Many pages have client-side checks for all sorts of things. Twitter, for example, used to check new passwords against a list of common passwords client-side. By opening the JavaScript you could see a list of passwords that Twitter does not allow.
Modify URLs
The internet uses Universal Record Locators (URLs) to express to computers where the user wants to go. We are used to clicking on links or searching and then clicking on links. But it is quite possible to navigate large parts of the internet by just directly editing URLs.
Software:
This activity will work on any major browser, and any other browser that allows you to edit URLs, including mobile browsers.
Steps
Amazon
Amazon uses a consistent naming structure across all their country-specific sites.
- Search amazon.com (USA Amazon) for a product of your choice.
- Add “&s=price-asc-rank” to the end of the URL and hit enter. What changed about the page?
- Open a product of your choice.
- Edit the domain from “amazon.com” to “amazon.ca” directly in the URL bar and hit enter.
- If the product is available in both the USA and Canada, then you should see the page change to the Canada version which will likely have a different price, shipping time, and somtimes different reviews.
- Amazon product URLs are long, but they actually don’t have to be. Starting at the rightmost end of the product’s URL, start deleting bits of the URL till you find the shortest URL that will still load the product page. It helps to think about how the URL is structured while doing the activity.
Wikipedia
Wikipedia uses a very accessable naming structure. If you know what you want, there is no need to even search, you can just enter the URL directly.
- The Wikipedia page for the University of Toronto is: https://en.wikipedia.org/wiki/University_of_Toronto
- Try creating a URL that links to the University of Waterloo’s Wikipedia page and then enter that URL directly into your browser’s URL bar to check if you did it correctly.
- Try creating at least one other Wikipedia URL and directly visiting it.
YouTube
YouTube includes information in the URL like distance through the video so that people can share not only videos, but specific points in videos. Since the information is in the URL, it can be manipulated.
- Open this wonderful video of Dr Vaniea lecturing on ethics. https://www.youtube.com/watch?v=GZniJBygnX8&t=133s
- Try jumpping to different points in the video by modifying the URL.
Reflection questions
- Have you ever tried directly modifying URLs before?
- What most supprised you about this activity?
Other things to try
- Try changing how you write URLs for git and for ssh.
- Lookup YouTube random video generators
Learn more
Dr Vaniea does research on URLs and how people read (or can’t) read them. Below are some of her research papers:
Read a Regulation, Law, or Advisory
Legal regulations can have large impacts on how technology is implemented. Laws and regulations are a way that government tries to influence how technology is built and how it impacts people.
In this activity you will be picking a regulation/law (suggestions below) and reading part of it.
Laws and regulations
Select a law/regulation from the following list. Or use this list as inspiration and select your own regulation to read. I encourage exploring Canadian regulation, but you are welcome to select from regulations worldwide as long as they have a clear connection to privacy or security.
Reflection questions
- Did you feel that you were able to understand the part of the regulation you read?
- As an Engineer, do you feel like you could implement what you read?
See data visible to websites
Your web browser provides lots of facts to webpages and to JavaScript as part of normal operations. These facts are helpful in that they let pages properly adapt content to match the capabilities of the computer and monitor they are on. But they can also be used to uniquely fingerprint and track users.
In this activity you will be looking at the types of information visible
Steps
- Visit the Cover Your Tracks website using your normal web browser using your normal settings. Click “Test Your Browser”.
- Make sure to scroll down on the results page to see all the different types of data the site was able to collect about your browser.
- Try visiting the page again using a privacy-preserving mode like Private Browsing, or Incognito.
- Try visiting with a different browser than your normal one.
- Brave
- Chrome - Advertising friendly
- Firefox - Auto blocks advertising
Reflection questions
- What detected information most supprised you.
Learn more
Verify a website certificate
We often visit websites and simply assume that the website we are seeing is the real one. But that is not always the case and for important websites you might want to do some verification. Man in the Middle Attacks can and do happen so web browsers use certificate authorities to verify the identity of websites. You have the ability to see these checks.
Steps
The following steps are written for Firefox but similar steps will work on most modern browsers.
- Visit a website that is likely to pay for enhanced verification. Unfortunately not many sites, even banks, do this, so I recommend trying one of the following first to see what enhanced verification looks like and then trying other possibilities:
- Look at the identity information. In Firefox:
- Click on the lock icon.
- You should see “Certificate issued to:” followed by the organization’s name. If this information is missing, then the organization has not paid for enhanced verification.
- Click on “Connection secure” to see more details. Note that now the full name and address are shown.
- Click on “More information” -> “View Certificate”
- This page lists the certificate chain that verifies this website. On the left is the organization’s certificate which has been signed. Then the certificate authorities that did the verification.
- Look in the “Certificate Policies” section where it should say “Domain Validation”, “Organization Validation”, or “Extended Validation”.
- Now try visiting a site that is likely less willing to pay for enhanced verification but is still relatively large. Below are some suggestions:
- Compare the “Subject Name” section of certificates of pages with and without enhanced verification.
- Finally, try visiting some pages that are small and use the “free tier” of certificates. Some suggestions:
Reflection questions
- How did the websites and certificates in the pages you looked at differ?
- What did you learn about how companies express their identity to end users?
- Few sites pay for extended validation. Is that a rational choice for companies to make?
Listen to Phish
This activity requires you (or someone physically near you) to receive a scam communication. So I recommend starting this activity a bit earlier than others since it is hard to control when a scam might happen. If you really don’t receive any scams, try talking to your friends or family about ones they have seen recently.
All you need to do is read or listen to the full scam communication and then think critically about the following questions. There is no need to progress past the initial communication. It is fine to hang up after the initial pitch by them, you do not need to speak to anyone, and you do not need to click any links. Please also review the safety guidance below.
Questions to think about
- Who is the scammer claiming to be?
- What would a real communication from that group or individual look like? (It is ok to answer that you do not know.)
- How did you determine this was a scam/phishing?
- What do you think the scammer is trying to achieve? This one may be challenging to impossible to answer, but trying guessing.
- How confident are you in your assessment? Could you be wrong?
- If you are unsure, how might you double check if the communication is valid or phishing?
Safety
Do not:
- Give out real data
- Click on links in suspected scams/phishing (unless you are on a safe VM, and even then be very careful)
- Give them your real name or contact details
- Email them back - many email providers (though maybe not UWaterloo) use Greylisting where the mail server considers if you have ever emailed the sender before when creating its spam score. The reasoning is that you normally only email valid contacts. But if you email a scammer, then the next email they send will get a score boost from the greylist and consequently may not catch a subtle scam. Avoid emailing scammers.
You can:
- Run wget on any links and look at the resulting page in a text editor. Do not open it with a web browser.
- Give the scammer a fake name or address
- Avoid using the contact information of the University you attend. Better to pick a large location in a populous city like Toronto.
- Talk vocally to the scammer. There is some risk that by answering you may git put on a “willing to answer” scammer list. But otherwise just talking to a scammer is not harmful if you pay attention to the rules above.
Reflection questions
- Answer the questions above.
- Add at least one sentence of self-reflection.
Learn more
Scams are often obvious because they occur outside the context we expect. That makes them easy to identify. But scams work by finding one person where that message does make sense. And just about anyone can fall for phishing:

