Human in the Loop
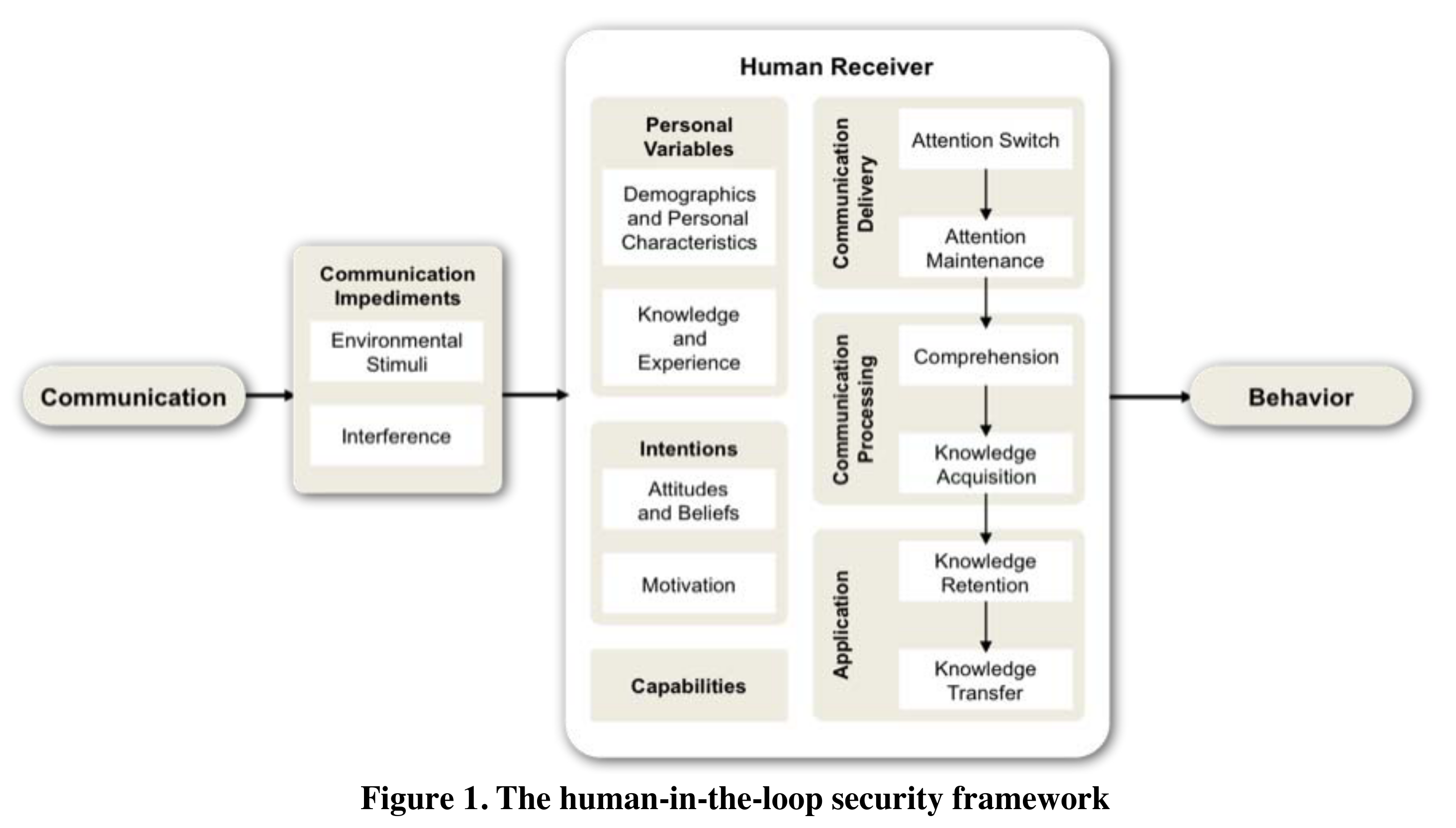
Human-in-the-loop security framework
Slides
Required Reading
- A framework for reasoning about the human in the loop by Lorrie Cranor
Learning Outcomes
Topics
- Human in the Loop Framework
Understand
- How to break down why a security or privacy warning is failing to engage users as intented.
Apply
- Screenshot a warning that you have seen and post it on the Piazza thread
Additional Resources
-
Warning Design Guidelines by Lujo Bauer, Cristian Bravo-Lillo, Lorrie Cranor, and Elli Fragkaki
-
Reeder, Rob, Ellen Cram Kowalczyk, and Adam Shostack. “Poster: Helping engineers design NEAT security warnings.” SOUPS, 2011.
-
Introducing the cybersurvival task: assessing and addressing staff beliefs about effective cyber protection by Nicholson, James, Lynne Coventry, and Pam Briggs
-
Riegelsberger, Jens, M. Angela Sasse, and John D. McCarthy. “The mechanics of trust: A framework for research and design.”
Papers on Advice
-
So long and no thanks for the Externalities: The rational rejection of security advice by end users by Cormac Herley
-
"… No one Can Hack My Mind": Comparing Expert and Non-Expert Security Practices by Ion, Iulia, Rob Reeder, and Sunny Consolvo
-
Tran, Mindy, et al. “Security, Privacy, and Data-sharing Trade-offs When Moving to the United States: Insights from a Qualitative Study.” 2024 IEEE Symposium on Security and Privacy (SP). IEEE Computer Society, 2023.
-
Maia J. Boyd, Jamar L. Sullivan Jr., Marshini Chetty, and Blase Ur. 2021. Understanding the Security and Privacy Advice Given to Black Lives Matter Protesters. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems (CHI ‘21). Association for Computing Machinery, New York, NY, USA, Article 549, 1–18.
-
Redmiles, Elissa M., Sean Kross, and Michelle L. Mazurek. “How I learned to be secure: a census-representative survey of security advice sources and behavior.” Proceedings of the 2016 ACM SIGSAC conference on computer and communications security. 2016.